Decentralized exchange aggregator Dexible suffered a $2 million exploit early Friday, the protocol said in a document posted on its Discord server.
Dexible tweeted that the hacker exploited a weakness in the smart contract code, allowing them to drain funds from crypto wallets with funds that have been approved for spending.
The team added that “a few whales,” meaning large crypto holders, accounted for about 85% of the losses.
Blockchain data shows that digital asset investment firm BlockTower Capital was among the victims.
The wallet address associated with the Dexible exploiter on blockchain monitoring platform Etherscan drained some $1.5 million in TRU tokens from a wallet labeled as BlockTower’s by Arkham Intelligence, a blockchain intelligence firm. Blockchain intelligence firm Nansen also labeled the address as BlockTower Capital’s.
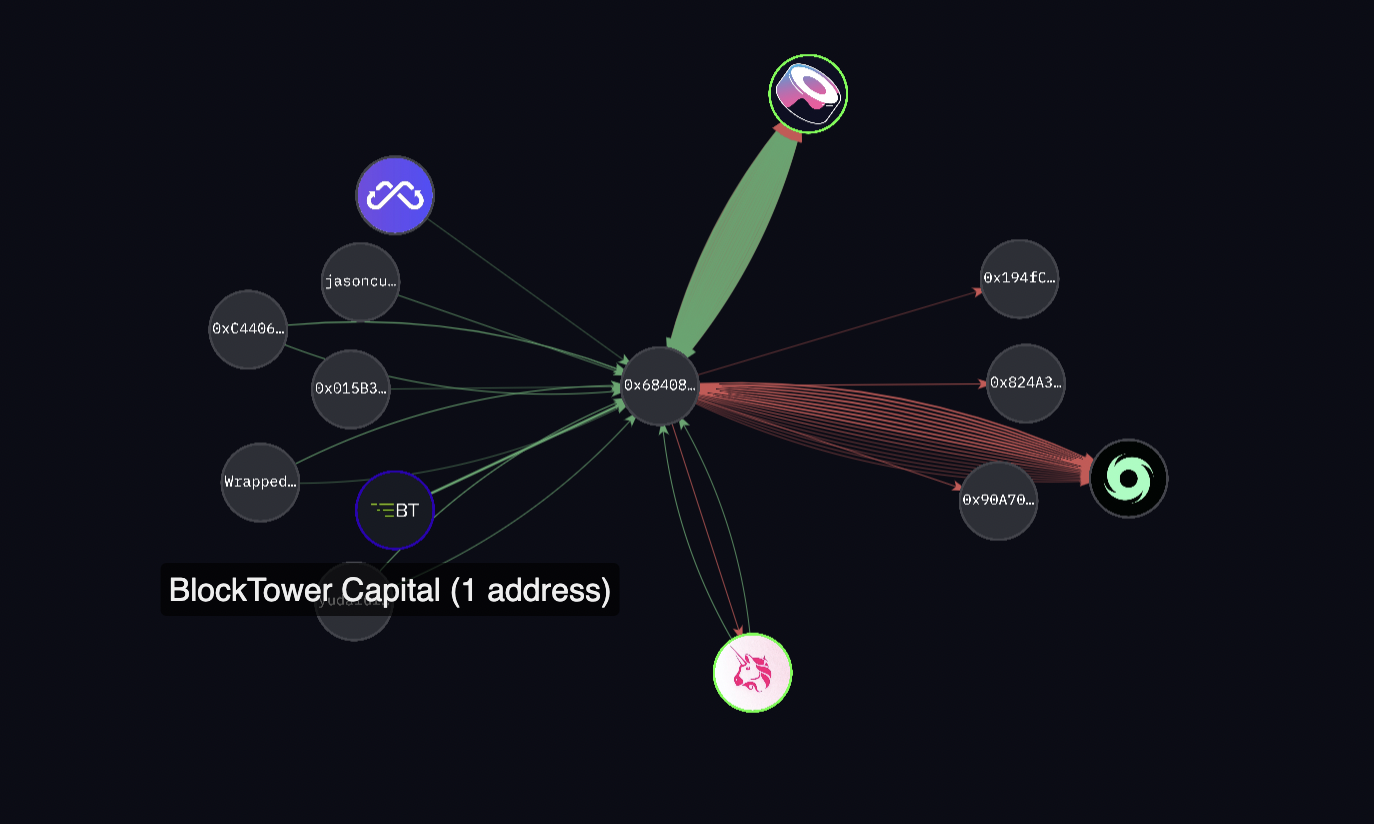
The Dexible exploiter traded the stolen funds for ETH using SushiSwap, then transferred the funds to TornadoCash. (Arkham Intelligence)
BlockTower did not immediately return CoinDesk’s request for comment.
Blockchain transactions on Arkham show that the exploiter transferred the stolen TRU tokens to SushiSwap to trade for ether (ETH). Then, they send ETH to crypto mixer service provider TornadoCash.
The exploit affected 13 wallets on Arbitrum and five wallets on Ethereum, draining a total of per Dexible’s report.
“We have paused these contracts, while we get a full picture of the situation,” Michael Coon, chief executive of Dexible, posted on Discord.



















